- Table of Contents
- 1. Introduction
- 2. The Evolving Cyber Threat Landscape
- From Opportunistic to Sophisticated Attacks
- Phishing
- Ransomware
- Insider Threats
- Supply Chain Vulnerabilities
- Global Statistics
- 3. The Cost of Cyber Negligence
- Financial Losses
- Hidden Costs
- Brand Reputation and Trust
- Case Study: Equifax
- 4. Cybersecurity as a Business Priority
- Not Just an IT Issue
- Risk Management, Compliance, and Governance
- Link to ESG and Corporate Responsibility
- 5. Human Factor: The Weakest Link or Strongest Defence
- Employee Errors
- Training and Awareness Campaigns
- Building a Cyber-Responsible Culture
- 6. Legal, Regulatory, and Compliance Pressures
- GDPR
- HIPAA
- CCPA
- ISO Standards
- Fines and Penalties
- Proactive Compliance
- 7. Cybersecurity and Remote/Hybrid Work
- Remote Access Risks
- BYOD and Device Management
- Cloud Vulnerabilities
- Best Practices
- 8. Cybersecurity and Customer Trust
- Damaging Confidence
- Cybersecurity as Competitive Advantage
- Examples
- 9. Emerging Technologies and New Risks
- AI-Driven Attacks
- Deepfakes
- IoT Vulnerabilities
- Risks in Cloud, Blockchain, and Smart Systems
- Preparing for Next-Gen Threats
- 10. Building a Cybersecurity-First Culture
- Leadership’s Role
- Password Management
- Incident Response Plans
- Zero-Trust Architecture
- Continuous Monitoring and Accountability
- 11. Practical Steps to Prioritise Cybersecurity
- Cybersecurity Frameworks
- Investments in Tools
- Incident Response Planning
- 12. Conclusion
1. Introduction
Cybersecurity has traditionally been perceived as a technical domain handled exclusively by IT departments. Firewalls, antivirus software, and server patches once defined the boundaries of protection. However, in the modern workplace, this narrow definition falls short. Cybersecurity is no longer merely a technology issue—it has become an organisation-wide responsibility that influences operations, culture, and long-term sustainability. Every employee, from the C-suite to frontline staff, plays a role in safeguarding digital and physical assets.
The urgency for organisations to prioritise cybersecurity is underlined by a rising global threat landscape. Cybercrime has evolved into a lucrative industry, with attackers developing highly sophisticated tools to exploit vulnerabilities in both systems and human behaviour. Phishing campaigns, ransomware attacks, and insider threats have disrupted businesses worldwide, while regulators continue to impose stricter penalties for negligence.
Ransomware, in particular, has become a defining challenge. Criminal groups are no longer content with encrypting files; they now threaten to leak sensitive data unless organisations pay hefty sums. Small and medium-sized enterprises (SMEs), once overlooked, are increasingly targeted, as cybercriminals recognise that these businesses often lack mature defences.
Cybersecurity must therefore be central to every workplace’s priorities—not as a cost centre, but as a strategic investment. The consequences of neglect are not limited to financial penalties; they extend to reputation, customer trust, and even survival in competitive markets. By embedding cybersecurity into everyday operations and strategic planning, businesses can protect not only their assets but also the trust of employees, clients, and stakeholders.
This article explores why cybersecurity deserves to be treated as a top workplace priority, analysing threats, costs, compliance requirements, and cultural imperatives. It also offers practical steps for leaders and employees to build resilience in an age where digital risk is inseparable from business continuity.
2. The Evolving Cyber Threat Landscape
From Opportunistic to Sophisticated Attacks
In the past, cybercriminals often relied on indiscriminate attacks, sending spam emails or exploiting common system vulnerabilities. Today, threats are more targeted and sophisticated. Advanced persistent threats (APTs) aim at specific industries or companies, often backed by organised crime groups or even nation-states. These adversaries conduct reconnaissance, exploit supply chains, and sometimes remain undetected for months.
Phishing
Phishing remains one of the most common and dangerous threats. Cybercriminals use deceptive emails, texts, or websites to trick employees into revealing credentials or downloading malware. Verizon’s 2023 Data Breach Investigations Report found that 36% of breaches involved phishing.
Ransomware
Ransomware has escalated dramatically in frequency and impact. Attackers not only lock access to data but also engage in double extortion—threatening to publish confidential files if payment is not made. The 2021 Colonial Pipeline attack disrupted fuel supply across the U.S., highlighting how ransomware can cripple critical infrastructure.
Insider Threats
Employees—whether malicious or negligent—represent a significant risk. Accidental misconfigurations, weak passwords, or deliberate theft of data can all compromise workplace security. Insider threats account for roughly 22% of incidents, according to Ponemon Institute.
Supply Chain Vulnerabilities
Modern organisations depend on a network of suppliers and service providers. Attacks targeting these third parties can have cascading effects. The SolarWinds breach in 2020 exposed multiple U.S. government agencies and corporations, illustrating the magnitude of supply chain risks.
Global Statistics
The following table summarises recent statistics:
Threat Type | Prevalence/Impact (2023) | Source |
Phishing | 36% of breaches | Verizon DBIR |
Ransomware | $20B global damages | Cybersecurity Ventures |
Insider Threats | 22% of incidents | Ponemon Institute |
Supply Chain Attacks | 66% of firms affected | BlueVoyant |
These evolving threats demonstrate that no organisation, regardless of size, is immune.
3. The Cost of Cyber Negligence
Financial Losses
Cyberattacks carry direct costs including ransom payments, regulatory fines, and business interruption. For SMEs, even a single breach can result in bankruptcy. A downtime of just one hour can cost large organisations hundreds of thousands of dollars.
Hidden Costs
Beyond the obvious financial damage, breaches create hidden costs: reduced employee productivity, prolonged downtime, and loss of strategic advantage. Equally significant is the erosion of customer trust, which can take years to rebuild.
Brand Reputation and Trust
Consumers are increasingly aware of cybersecurity risks. A breach may cause customers to abandon a brand permanently. Trust is difficult to restore once clients doubt a company’s ability to safeguard personal or financial data.
Case Study: Equifax
In 2017, Equifax suffered a breach that exposed the personal data of 147 million people. The incident led to $1.4 billion in total costs, lawsuits, and long-term damage to its reputation. Beyond the monetary impact, Equifax faced immense public scrutiny that continues to shape how organisations approach cybersecurity.
The lesson is clear: cyber negligence is not a technical oversight—it is a critical business failure with wide-ranging consequences.
4. Cybersecurity as a Business Priority
Not Just an IT Issue
Cybersecurity has long been siloed within IT departments, where firewalls, patching, and malware detection dominated the conversation. However, modern workplaces operate on interconnected digital ecosystems where every department is a potential entry point for attackers. For instance, HR departments manage large volumes of sensitive employee data, including payroll information, which can be exploited through phishing or credential theft. Marketing teams rely on customer databases and digital campaigns that can be targeted by social engineering attacks. Finance teams face the risk of fraudulent transfers or compromised financial reporting systems, while executives carry the burden of making strategic decisions under the scrutiny of stakeholders and regulators.
Limiting cybersecurity responsibility to IT teams undermines resilience, as threats often arise through non-technical pathways such as human error, supplier compromise, or reputational manipulation online. To be effective, cybersecurity must therefore be embedded into every business process and role—a mindset shift that strengthens resilience across the organisation.
Risk Management, Compliance, and Governance
In today’s environment, cyber risks are business risks, not just technical ones. Boards and executive teams are increasingly required to treat cybersecurity with the same gravity as financial, operational, or reputational risk. Integrating cybersecurity into risk management frameworks allows businesses to identify vulnerabilities, quantify their impact, and develop mitigation strategies.
Corporate governance structures must also evolve to include clear cybersecurity oversight. For example, many organisations are establishing board-level committees dedicated to technology and security. This ensures that cyber risks are regularly discussed at the highest level, budgets are allocated appropriately, and accountability for breaches is transparent.
Link to ESG and Corporate Responsibility
Cybersecurity also intersects with broader ESG (Environmental, Social, Governance) commitments. Under the social dimension, protecting personal data and respecting digital privacy are increasingly seen as basic human rights. Under the governance dimension, demonstrating cyber resilience is part of responsible corporate leadership. Investors, rating agencies, and even customers now factor in how well organisations manage digital risk when evaluating long-term sustainability.
For example, firms that obtain ISO 27001 certification or publish annual cybersecurity reports often score higher in ESG assessments, making them more attractive to investors. By aligning cybersecurity with ESG, organisations demonstrate not only compliance but also a proactive commitment to ethical governance and stakeholder trust.
5. Human Factor: The Weakest Link or Strongest Defence
Employee Errors
Despite technological defences, human error remains the leading cause of breaches. Common mistakes include falling for phishing scams, reusing weak passwords across multiple platforms, or mishandling sensitive data on unsecured devices. Verizon’s Data Breach Investigations Report (2023) revealed that 82% of breaches involved a human element, either through negligence or malicious insider activity.
Even senior executives are not immune. Business Email Compromise (BEC) scams, where attackers impersonate executives to authorise fraudulent payments, continue to cost organisations billions annually.
Training and Awareness Campaigns
The solution lies in sustained and engaging training. Traditional one-time workshops or compliance tick-box exercises are rarely effective. Instead, interactive training programmes —such as phishing simulations, role-playing exercises, and gamified learning platforms—help employees internalise safe behaviours. Training should be continuous, evolving with emerging threats, and tailored to specific roles. For instance, finance staff should receive additional training on spotting fraudulent invoices, while HR personnel need to learn how to secure candidate and employee records.
Building a Cyber-Responsible Culture
Beyond skills, a culture of responsibility must be cultivated. Employees should feel empowered to report suspicious activity without fear of blame or punishment. Leaders can encourage this by recognising secure behaviours, sharing stories of how vigilance prevented attacks, and embedding cybersecurity into everyday communication.
When cybersecurity becomes a shared value rather than a burdensome task, employees transform from vulnerabilities into defenders. In organisations that prioritise culture, staff are more likely to question suspicious requests , use secure tools, and actively protect both company and customer data.
6. Legal, Regulatory, and Compliance Pressures
GDPR
The General Data Protection Regulation (GDPR) in the European Union sets one of the highest global standards for data protection. It mandates that organisations safeguard personal data and report breaches within 72 hours. Penalties can be staggering—up to €20 million or 4% of global annual turnover, whichever is higher. This law has reshaped how businesses worldwide handle personal data, not just in Europe but also for any company serving EU residents.
HIPAA
In the United States, the Health Insurance Portability and Accountability Act (HIPAA) governs patient health data. Healthcare organisations are obligated to implement strict safeguards around electronic health records. Non-compliance can lead to civil and criminal penalties, as well as reputational damage in a sector where trust is paramount.
CCPA
The California Consumer Privacy Act (CCPA) gives consumers the right to know what personal data businesses collect, how it is used, and the ability to opt out of its sale. For companies, compliance requires new levels of transparency and robust systems for handling customer requests. With similar laws emerging in other states, CCPA has set a precedent for stricter consumer protections across the U.S.
ISO Standards
Global standards such as ISO/IEC 27001 provide structured frameworks for building Information Security Management Systems (ISMS). While voluntary, certification demonstrates a company’s commitment to cybersecurity, often serving as a competitive differentiator in winning contracts or meeting vendor requirements.
Fines and Penalties
Non-compliance is costly. In 2021, Amazon was fined €746 million under GDPR for failing to meet transparency obligations. Such high-profile cases emphasise that even the largest corporations are not immune.
Proactive Compliance
Forward-thinking organisations treat compliance not as a box-ticking exercise but as an opportunity to build trust and resilience. By adopting stricter standards voluntarily, businesses not only avoid penalties but also strengthen customer and investor confidence. Compliance then becomes a competitive advantage rather than a liability.
7. Cybersecurity and Remote/Hybrid Work
Remote Access Risks
The rapid shift to remote work exposed organisations to a surge in vulnerabilities. Employees often access corporate networks via unsecured home Wi-Fi, public hotspots, or shared family devices. Cybercriminals exploit these weak points through credential stuffing, malware injection, or man-in-the-middle attacks.
BYOD and Device Management
Bring Your Own Device (BYOD) policies offer flexibility but also increase complexity. Personal devices may lack up-to-date security patches, run outdated software, or host unvetted apps. Without strong device management protocols—such as Mobile Device Management (MDM)—these endpoints become prime attack vectors.
Cloud Vulnerabilities
Remote and hybrid work rely heavily on cloud applications for file sharing, video conferencing, and project management. While cloud providers secure infrastructure, businesses remain responsible for access control and data handling under the shared responsibility model . Misconfigurations, such as leaving storage buckets exposed, have led to high-profile breaches.
Best Practices
To reduce risks, organisations must adopt a layered security approach:
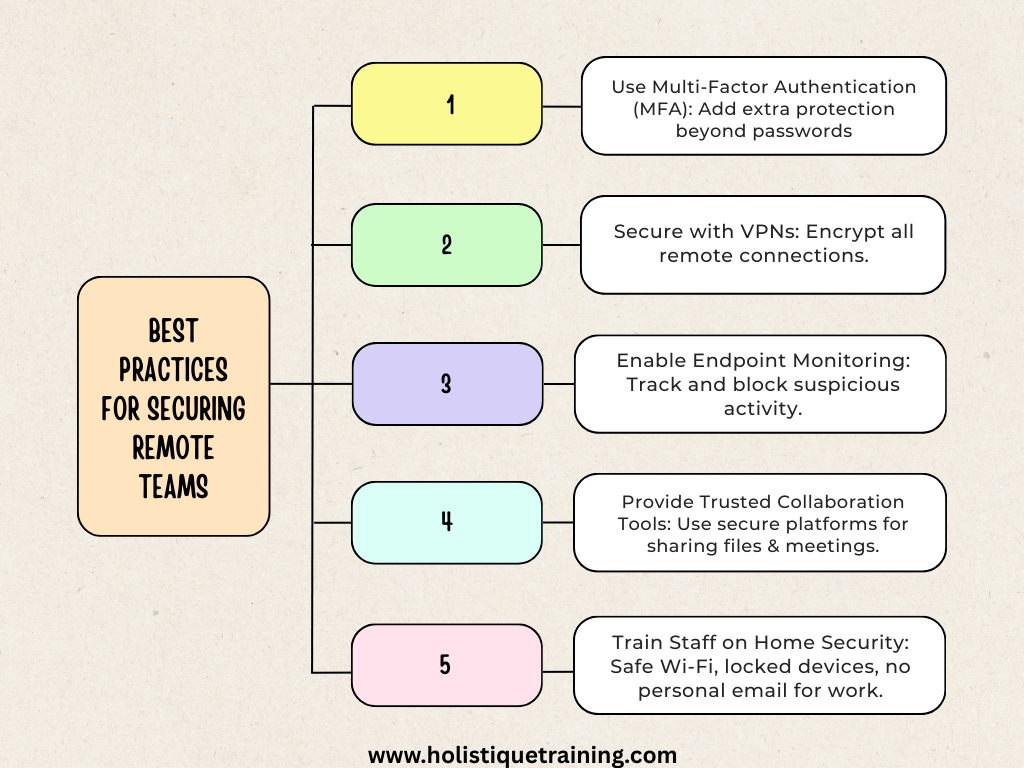
- Multi-Factor Authentication (MFA): Adds an extra barrier against stolen credentials.
- VPNs and Endpoint Monitoring: Encrypt communications and monitor suspicious activity across devices.
- Secure Collaboration Tools: Platforms like Microsoft Teams or Slack should be configured with appropriate security policies.
- Home-Office Security Training: Employees must learn to secure routers, avoid personal email for work, and lock devices when unattended.
By adopting these practices, businesses can extend their security perimeter beyond the office walls. In a world where hybrid work is here to stay, protecting distributed teams is not optional—it is central to organisational resilience.
8. Cybersecurity and Customer Trust
Damaging Confidence
Breaches not only expose data but also shatter customer trust. Research by PwC shows 85% of consumers will not engage with a business if they have concerns about security.
Cybersecurity as Competitive Advantage
Companies that demonstrate robust protection gain a market edge. Cybersecurity becomes part of the value proposition, especially in industries such as finance and e-commerce.
Examples
Apple: Known for its emphasis on privacy, Apple markets security as a differentiator.
Microsoft: Investment in zero-trust frameworks has bolstered enterprise trust in its cloud services.
Strong security translates into stronger brand loyalty.
9. Emerging Technologies and New Risks
AI-Driven Attacks
Attackers increasingly use AI to craft convincing phishing campaigns, automate attacks, and bypass traditional defences.
Deepfakes
Deepfake technology poses risks of misinformation, fraud, and reputational attacks against businesses and executives.
IoT Vulnerabilities
The explosion of IoT devices creates new entry points. Poorly secured devices can be exploited to launch large-scale attacks.
Risks in Cloud, Blockchain, and Smart Systems
While innovative, these technologies introduce new risks. Misconfigured cloud services, flawed blockchain implementations, and insecure smart devices can all be exploited.
Preparing for Next-Gen Threats
Investing in AI-driven defences, continuous monitoring, and proactive research ensures organisations stay ahead of attackers.
10. Building a Cybersecurity-First Culture
Leadership’s Role
Executives must champion cybersecurity as a strategic priority, allocating budgets and resources, and setting measurable goals.
Password Management
Strong password policies, coupled with password managers and MFA, reduce the likelihood of breaches.
Incident Response Plans
A well-documented and rehearsed plan ensures swift recovery from attacks. It should define roles, escalation paths, and communication strategies.
Zero-Trust Architecture
The zero-trust model assumes no user or device is inherently trustworthy. Continuous verification and least-privilege access reduce exposure.
Continuous Monitoring and Accountability
Regular audits, penetration tests, and transparent reporting build resilience. Holding employees accountable fosters vigilance.
A culture-first approach integrates security into every process, decision, and behaviour.
11. Practical Steps to Prioritise Cybersecurity
Cybersecurity Frameworks
Frameworks such as NIST Cybersecurity Framework and CIS Controls provide structured approaches to assess risks and implement defences.
Investments in Tools
Organisations should invest in next-generation firewalls, endpoint detection and response (EDR), and MFA solutions.
Incident Response Planning
Regular testing of incident response ensures preparedness. Incorporating cyber insurance provides an additional financial safeguard.
Step | Purpose |
Adopt frameworks | Structured, industry best-practice |
Invest in tools | Enhance detection & protection |
Train staff | Reduce human errors |
Cyber insurance | Offset financial risk |
Practical implementation ensures that cybersecurity evolves from a theoretical goal to a daily operational reality.
12. Conclusion
Cybersecurity is no longer an optional investment but a workplace necessity. With threats growing in sophistication and frequency, organisations face significant financial, legal, and reputational risks if they fail to act. From phishing to ransomware, insider threats to supply chain vulnerabilities, the evolving landscape demands vigilance and preparedness.
The costs of negligence are severe, ranging from direct financial losses to irreparable damage to trust. Yet, proactive businesses that embed cybersecurity into their governance, culture, and daily operations not only protect themselves but also gain a competitive edge. Compliance with global regulations, investment in training, and adoption of modern security frameworks build both resilience and reputation.
Ultimately, cybersecurity is a shared responsibility. Leadership must provide vision and resources, employees must embrace secure practices, and IT must maintain robust defences. Together, these efforts form a cohesive shield against evolving threats.
Looking forward, cybersecurity will increasingly define workplace sustainability. Organisations that view it as a core strategic priority will be best positioned to thrive in the digital economy. Those that neglect it risk not only financial collapse but also the erosion of trust that underpins every successful enterprise.